
Did hacked CCTV cameras really break the internet?
If you were unable to access your favourite website last Thursday, then you weren’t alone. As has now been widely reported, a vast swathe of some of the internet’s most popular sites were taken down after a huge cyber attack targeted New Hampshire based internet infrastructure giant Dyn. The company’s technology underpins a huge number of websites, most of which were inaccessible across many countries for a large part of the day. Whilst some office managers were arguably relieved at Reddit and Twitter being down for the afternoon, it was an ominous sign of just much damage a well planned attack can reap on an infrastructure that is now central to most of the world’s communications.
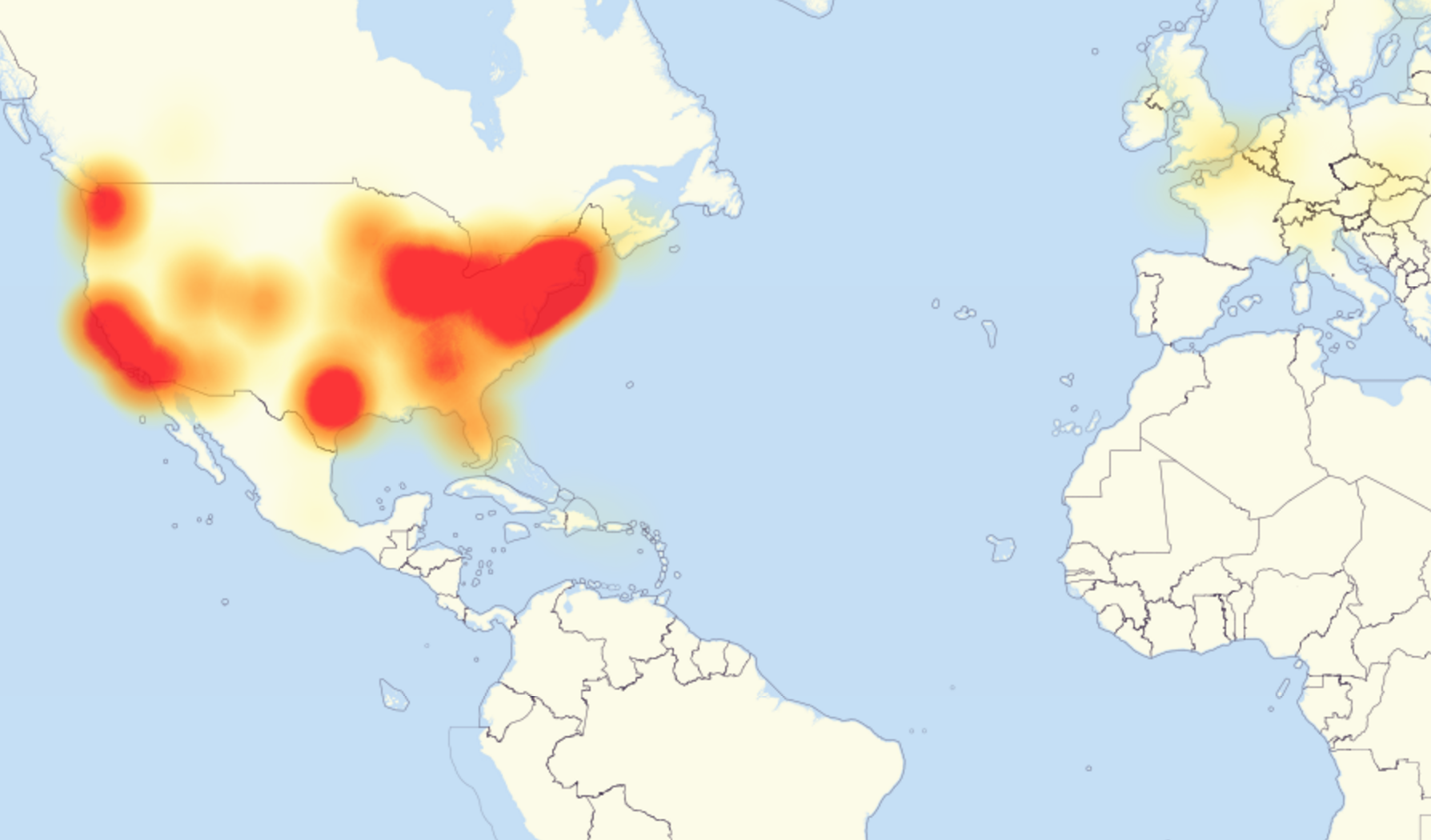
In the days after the attack however, some headlines started emerging that raised eyebrows in the home security industry- many attributed the attack to hacked CCTV cameras. But how could that happen? And what implications does it have for your own home CCTV systems?
What is a DDoS attack?
Like many high profile cyber attacks, Dyn was brought down by a distributed denial-of-service, or “DDoS” attack. This is where a hacker deliberately directs huge amounts of meaningless traffic to a website, flooding it’s severs with requests that make them inaccessible for actual users. It’s essentially the advanced online equivalent of tying up a company’s phone line with prank calls. In order for the attack to work, the traffic must be directed from many different IP addresses at once, both to hide the identity of the attacker and to prevent the site owners from easily blocking the traffic. This is where the CCTV cameras (and many other devices) came into play.
One of the ways in which hackers can run a DDoS attack is to create a “botnet”- a network of computers that they can remotely control, and use to automate an attack. With the advent of the so-called “internet-of-things”, half of the world’s CCTV cameras, toasters, fridges and thermostats now include built-in computers with network connections. Using malware, hackers can take control of many of these devices, and use them as part of their botnets. In the case of the Dyn attack, it appears that tens of millions the traffic sources were involved, with many of them being hacked CCTV and webcams from a Chinese manufacturer called Xiongmai.
New technology, old risk?
With the huge proliferation of smart devices over the last few years, most of the focus has understandably been on the vastly improved functionality that they give us. Now we can turn on our heating, watch our pets, or check the food in our fridge wherever we are. With this increased connectivity however, comes an inherent risk- an one that security researchers are increasingly sounding the alarm over. Across all of the manufacturers producing these products, there are no common standards for security. As detailed in a great article on ZDNet, Many show serious vulnerabilities that desktop PCs patched up years ago, such as storing information in plain text formats.
These risks were recently made plain with the public release of hacking software known as “Mirai”. This scans networks for connected devices, and tries to gain access to them by using the manufacturer’s default login details. Researchers confirmed last week that Mirai was used in the Dyn attack, and made grave predictions as to how it could be used in the future.
So, what can we do?
Unfortunately, until manufacturers take up improved standards in security for these types of devices, this will always be an issue. Luckily, as a user, there is something incredibly easy you can do to make sure that your internet enabled CCTV camera or recorder cannot be used in this type of attack- CHANGE THE DEFAULT PASSWORD. Almost all of the malware the hackers use makes use of the fact that many people will purchase and install a device without changing it from the factory default login details. Simply by changing the password to something secure- preferably a combination of numbers and letters of different cases- you can prevent your system being involved.
featured image via

